YAMAHA1200を使うと簡単にIPsecによる拠点間VPNを作れます。
オフィスのVPNは拠点間で1つのファイルサーバを共有するのによく使いますが、最近ではクラウドとVPN接続してオフィスのネットワークを拡張するといったことも流行です。
もくじ
よくする手順
- ウィザードでLAN1のプライベートネットワーク設定
- LAN2のWANの設定
PPPoEならプロバイダ接続の設定を行う - そりゃやっぱり ぜったい がっちり 固定IPの方がイイ!
固定IPの確認 or ネットボランチ設定
固定IP ・・・そのままでよし!
PPPoE ・・・ネットボランチでホスト名の設定必要
※ネットワーク型プロバイダ接続型で固定IPでない契約の場合、
拠点間VPN(IPsec)は難しい・・・私は知らない。 - L2TP(VPN)でanonymousチャンネルの作成
これでSSHみたいに遠隔地のルータを操作出来ます。 - 機器を出荷します!!
- 出荷先の担当者にONUと機器のWANを接続して貰います。
これでL2TPでリモートから設定できるようになりました。 - 拠点間VPNの設定
L2TPでのVPN経由でGUIから拠点間VPN(IPsec)設定するのが楽
よくある設定でRTX1200で拠点間VPN組むならこの手順が安定しています。
A拠点
- LAN1
プライベートネットワーク:192.168.11.0/24 - LAN2(WAN)
ネットワーク型プロバイダ固定IP(NURO)
ip route default gateway dhcp lan2 ip route 192.168.10.0/24 gateway tunnel 2 ←B拠点への静的ルーティング(重要) ip keepalive 1 icmp-echo 10 5 dhcp lan2 ip lan1 address 192.168.11.1/24 ip lan1 proxyarp on ip lan1 secure filter in 100000 100001 100002 100003 100004 100005 100006 100007 100099 description lan2 PRV/DHCP/225:NURO_LAN2 ip lan2 address dhcp ip lan2 secure filter in 101003 101020 101021 101022 101023 101024 101025 101030 101032 101080 101081 101082 102001 102002 102003 102004 102005 ip lan2 secure filter out 101013 101020 101021 101022 101023 101024 101025 101026 101027 101099 dynamic 101080 101081 101082 101083 101084 101085 101098 101099 ip lan2 nat descriptor 200 ## L2TP pp select anonymous pp bind tunnel1 pp auth request mschap-v2 pp auth username yuu-user xxxxxxxx ←L2TPのanonymousアカウント ppp ipcp ipaddress on ppp ipcp msext on ip pp remote address pool dhcp ip pp mtu 1258 pp enable anonymous ## IPsec 拠点Bへの接続 tunnel select 1 tunnel encapsulation l2tp ipsec tunnel 1 ipsec sa policy 1 1 esp aes-cbc sha-hmac ipsec ike keepalive log 1 off ipsec ike keepalive use 1 off ipsec ike nat-traversal 1 on ipsec ike pre-shared-key 1 text hoge-key ←秘密鍵パスフレーズ ipsec ike remote address 1 any l2tp tunnel auth off l2tp keepalive use on ip tunnel tcp mss limit auto tunnel enable 1 tunnel select 2 description tunnel To-kyoten-B ipsec tunnel 2 ipsec sa policy 2 2 esp 3des-cbc md5-hmac ipsec ike keepalive use 2 auto heartbeat ipsec ike local address 2 192.168.11.1 ipsec ike pre-shared-key 2 text hoge-key ←秘密鍵パスフレーズ ipsec ike remote address 2 kyoten-b.aa0.netvolante.jp ←拠点Bホスト名 ip tunnel tcp mss limit auto tunnel enable 2 ip filter 100000 reject * * udp,tcp 135 * ip filter 100001 reject * * udp,tcp * 135 ip filter 100002 reject * * udp,tcp netbios_ns-netbios_dgm * ip filter 100003 reject * * udp,tcp * netbios_ns-netbios_dgm ip filter 100004 reject * * udp,tcp netbios_ssn * ip filter 100005 reject * * udp,tcp * netbios_ssn ip filter 100006 reject * * udp,tcp 445 * ip filter 100007 reject * * udp,tcp * 445 ip filter 100099 pass * * * * * ip filter 101000 reject 10.0.0.0/8 * * * * ip filter 101001 reject 172.16.0.0/12 * * * * ip filter 101002 reject 192.168.0.0/16 * * * * ip filter 101003 reject 192.168.11.0/24 * * * * ip filter 101010 reject * 10.0.0.0/8 * * * ip filter 101011 reject * 172.16.0.0/12 * * * ip filter 101012 reject * 192.168.0.0/16 * * * ip filter 101013 reject * 192.168.11.0/24 * * * ip filter 101020 reject * * udp,tcp 135 * ip filter 101021 reject * * udp,tcp * 135 ip filter 101022 reject * * udp,tcp netbios_ns-netbios_ssn * ip filter 101023 reject * * udp,tcp * netbios_ns-netbios_ssn ip filter 101024 reject * * udp,tcp 445 * ip filter 101025 reject * * udp,tcp * 445 ip filter 101026 restrict * * tcpfin * www,21,nntp ip filter 101027 restrict * * tcprst * www,21,nntp ip filter 101030 pass * 192.168.11.0/24 icmp * * ip filter 101031 pass * 192.168.11.0/24 established * * ip filter 101032 pass * 192.168.11.0/24 tcp * ident ip filter 101033 pass * 192.168.11.0/24 tcp ftpdata * ip filter 101034 pass * 192.168.11.0/24 tcp,udp * domain ip filter 101035 pass * 192.168.11.0/24 udp domain * ip filter 101036 pass * 192.168.11.0/24 udp * ntp ip filter 101037 pass * 192.168.11.0/24 udp ntp * ip filter 101080 pass * 192.168.11.1 esp * * ip filter 101081 pass * 192.168.11.1 udp * 500 ip filter 101082 pass * 192.168.11.1 udp * 4500 ip filter 101099 pass * * * * * ip filter 102001 pass * * gre * * ip filter 102002 pass * * tcp * 1723 ip filter 102003 pass * * udp * 500 ip filter 102004 pass * * esp ip filter 102005 pass * * udp * 4500 ip filter 500000 restrict * * * * * ip filter dynamic 101080 * * ftp ip filter dynamic 101081 * * domain ip filter dynamic 101082 * * www ip filter dynamic 101083 * * smtp ip filter dynamic 101084 * * pop3 ip filter dynamic 101085 * * submission ip filter dynamic 101098 * * tcp ip filter dynamic 101099 * * udp ## VPNに必要なパケットをNATに通す IKE(500), ESP暗号, IPsec NAT-T(4500),L2TP(1701)をルータが占有しNAT nat descriptor type 200 masquerade nat descriptor address outer 200 primary nat descriptor masquerade static 200 101 192.168.11.1 esp nat descriptor masquerade static 200 102 192.168.11.1 udp 500 nat descriptor masquerade static 200 104 192.168.11.1 udp 4500 ipsec auto refresh on ipsec transport 1 1 udp 1701 dhcp service server dhcp server rfc2131 compliant except remain-silent dhcp scope 1 192.168.11.2-192.168.11.150/24 dns server 8.8.8.8 4.4.4.4 dns server select 500226 8.8.8.8 4.4.4.4 any . dns private address spoof on snmp sysname yamaha-rtx1200-00a0de6a657d l2tp service on httpd host lan1 statistics cpu on statistics memory on
B拠点
- LAN1
プライベートネットワーク:192.168.10.0/24 - LAN2(WAN)
PPPoE(ビッグローブ)
ip route default gateway pp 1 ip route 192.168.11.0/24 gateway tunnel 2 ←A拠点への静的ルーティング(重要) ip lan1 address 192.168.10.1/24 ip lan1 proxyarp on ip lan1 secure filter in 100000 100001 100002 100003 100004 100005 100006 100007 100099 pp select 1 description pp PRV/PPPoE/0:biglobe pp keepalive interval 30 retry-interval=30 count=12 pp always-on on pppoe use lan2 pppoe auto disconnect off pp auth accept pap chap pp auth myname hoge@biglobe.ne.jp xxxxxxxx ←PPPoEアカウントとパスワード ppp lcp mru on 1454 ppp ipcp ipaddress on ppp ccp type none ip pp secure filter in 200003 200020 200021 200022 200023 200024 200025 200030 200032 200080 200081 200082 ip pp secure filter out 200013 200020 200021 200022 200023 200024 200025 200026 200027 200099 dynamic 200080 200081 200082 200083 200084 200085 200098 200099 ip pp nat descriptor 1000 # ネットボランチ netvolante-dns use pp server=1 auto netvolante-dns hostname host pp server=1 kyoten-b.aa0.netvolante.jp ←拠点Bネットボランチによるホスト名 ## L2TP pp enable 1 pp select anonymous pp bind tunnel1 pp auth request mschap-v2 pp auth username yuu-user xxxxxxxx ←L2TPのanonymousアカウント ppp ipcp ipaddress on ppp ipcp msext on ip pp remote address pool dhcp ip pp mtu 1258 pp enable anonymous tunnel select 1 tunnel encapsulation l2tp ipsec tunnel 1 ipsec sa policy 1 1 esp aes-cbc sha-hmac ipsec ike keepalive log 1 off ipsec ike keepalive use 1 off ipsec ike nat-traversal 1 on ipsec ike pre-shared-key 1 text hoge-key ←秘密鍵パスフレーズ ipsec ike remote address 1 any l2tp tunnel auth off l2tp keepalive use on ip tunnel tcp mss limit auto tunnel enable 1 ## IPsec 拠点Aへの接続 tunnel select 2 description tunnel To-kyoten-A ipsec tunnel 2 ipsec sa policy 2 2 esp 3des-cbc md5-hmac ipsec ike keepalive use 2 auto heartbeat ipsec ike local address 2 192.168.10.1 ipsec ike pre-shared-key 2 text hoge-key ←秘密鍵パスフレーズ ipsec ike remote address 2 aaa.xxx.yyy.zzz ←A拠点IPアドレス ip tunnel tcp mss limit auto tunnel enable 2 ip filter 100000 reject * * udp,tcp 135 * ip filter 100001 reject * * udp,tcp * 135 ip filter 100002 reject * * udp,tcp netbios_ns-netbios_dgm * ip filter 100003 reject * * udp,tcp * netbios_ns-netbios_dgm ip filter 100004 reject * * udp,tcp netbios_ssn * ip filter 100005 reject * * udp,tcp * netbios_ssn ip filter 100006 reject * * udp,tcp 445 * ip filter 100007 reject * * udp,tcp * 445 ip filter 100099 pass * * * * * ip filter 200000 reject 10.0.0.0/8 * * * * ip filter 200001 reject 172.16.0.0/12 * * * * ip filter 200002 reject 192.168.0.0/16 * * * * ip filter 200003 reject 192.168.10.0/24 * * * * ip filter 200010 reject * 10.0.0.0/8 * * * ip filter 200011 reject * 172.16.0.0/12 * * * ip filter 200012 reject * 192.168.0.0/16 * * * ip filter 200013 reject * 192.168.10.0/24 * * * ip filter 200020 reject * * udp,tcp 135 * ip filter 200021 reject * * udp,tcp * 135 ip filter 200022 reject * * udp,tcp netbios_ns-netbios_ssn * ip filter 200023 reject * * udp,tcp * netbios_ns-netbios_ssn ip filter 200024 reject * * udp,tcp 445 * ip filter 200025 reject * * udp,tcp * 445 ip filter 200026 restrict * * tcpfin * www,21,nntp ip filter 200027 restrict * * tcprst * www,21,nntp ip filter 200030 pass * 192.168.10.0/24 icmp * * ip filter 200031 pass * 192.168.10.0/24 established * * ip filter 200032 pass * 192.168.10.0/24 tcp * ident ip filter 200033 pass * 192.168.10.0/24 tcp ftpdata * ip filter 200034 pass * 192.168.10.0/24 tcp,udp * domain ip filter 200035 pass * 192.168.10.0/24 udp domain * ip filter 200036 pass * 192.168.10.0/24 udp * ntp ip filter 200037 pass * 192.168.10.0/24 udp ntp * ip filter 200080 pass * 192.168.10.1 esp * * ip filter 200081 pass * 192.168.10.1 udp * 500 ip filter 200082 pass * 192.168.10.1 udp * 4500 ip filter 200099 pass * * * * * ip filter 500000 restrict * * * * * ip filter dynamic 200080 * * ftp ip filter dynamic 200081 * * domain ip filter dynamic 200082 * * www ip filter dynamic 200083 * * smtp ip filter dynamic 200084 * * pop3 ip filter dynamic 200085 * * submission ip filter dynamic 200098 * * tcp ip filter dynamic 200099 * * udp ## VPNに必要なパケットをNATに通す IKE(500), ESP暗号, IPsec NAT-T(4500),L2TP(1701)をルータが占有しNAT nat descriptor type 1000 masquerade nat descriptor masquerade static 1000 101 192.168.10.1 esp nat descriptor masquerade static 1000 102 192.168.10.1 udp 500 nat descriptor masquerade static 1000 104 192.168.10.1 udp 4500 ipsec auto refresh on ipsec transport 1 1 udp 1701 dhcp service server dhcp server rfc2131 compliant except remain-silent dhcp scope 1 192.168.10.2-192.168.10.191/24 dns server 8.8.8.8 8.8.4.4 dns server select 500001 8.8.8.8 8.8.4.4 any . restrict pp 1 dns private address spoof on snmp sysname yamaha-rtx1200-00a0de672b09 l2tp service on statistics cpu on statistics memory on
GUIでIPsecを設定する
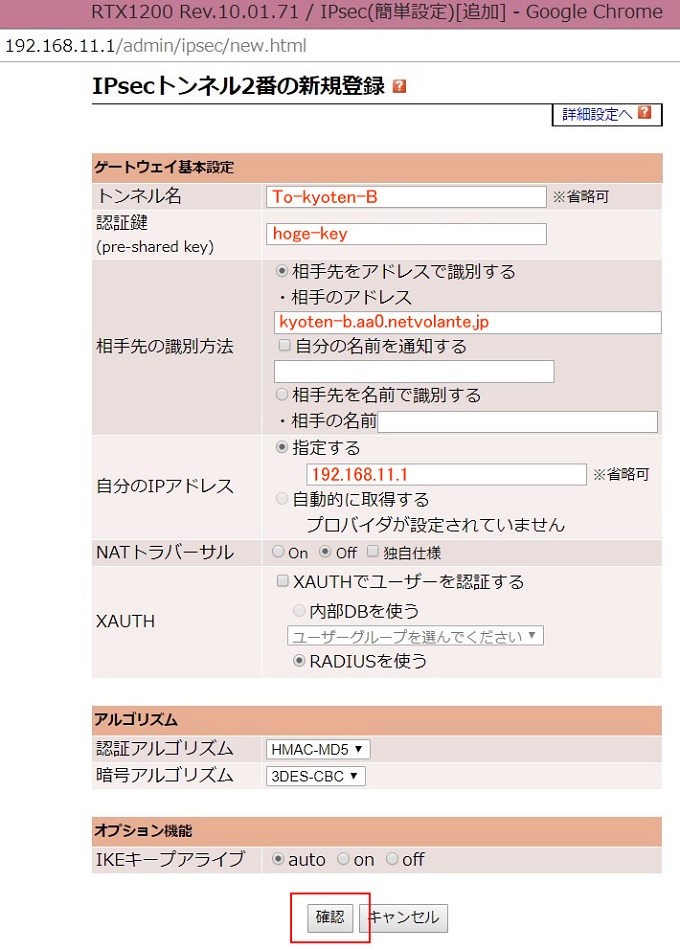
A拠点からB拠点へIPsecの設定を行います。
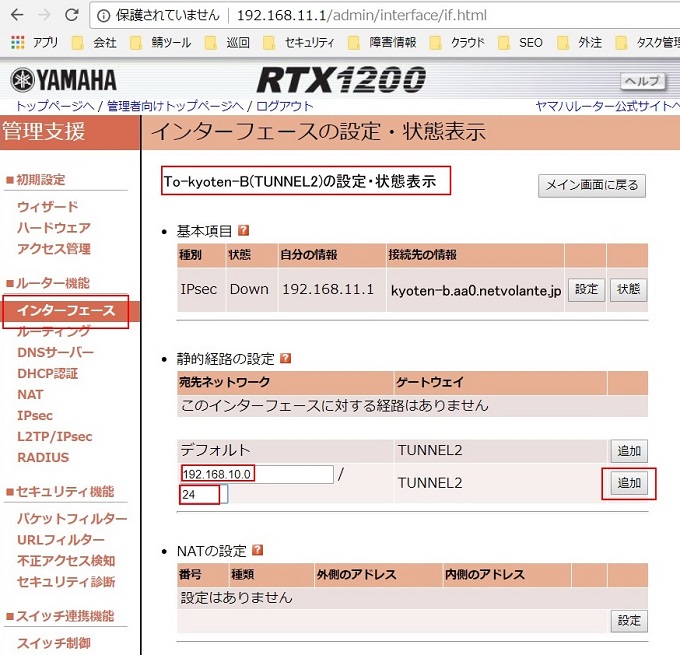
B拠点のIPsecを設定しているインターフェイスにB拠点の静的経路(192.168.11.10/24)の設定を追加します。
また、B拠点のルータでも同様にA拠点のIPsec設定を行います。A拠点とB拠点の設定が終わったわけです。そうするとステータスがUPになります。
お疲れ様です。






![[MysQL]オンラインDDL](https://www.yuulinux.tokyo/contents/wp-content/uploads/2020/04/mysql_logo-150x150.jpg)