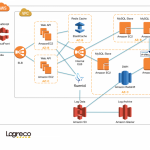
寄稿しました。
- ローカルルータのグローバルIP
118.xxx.yyy.253 - AWS VPC側 グローバルIP
13.112.141.58
52.197.214.91
Password: RTX1100 Rev.8.03.94 (Thu Dec 5 19:06:16 2013) Copyright (c) 1994-2012 Yamaha Corporation. All Rights Reserved. Copyright (c) 1991-1997 Regents of the University of California. Copyright (c) 1995-2004 Jean-loup Gailly and Mark Adler. Copyright (c) 1998-2000 Tokyo Institute of Technology. Copyright (c) 2000 Japan Advanced Institute of Science and Technology, HOKURIKU. Copyright (c) 2002 RSA Security Inc. All rights reserved. Copyright (c) 1997-2004 University of Cambridge. All rights reserved. Copyright (C) 1997 - 2002, Makoto Matsumoto and Takuji Nishimura, All rights reserved. Copyright (c) 1995 Tatu Ylonen , Espoo, Finland All rights reserved. Copyright (c) 1998-2004 The OpenSSL Project. All rights reserved. Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com) All rights reserved. Copyright (c) 2006 Digital Arts Inc. All Rights Reserved. 00:a0:de:34:a5:1d, 00:a0:de:34:a5:1e, 00:a0:de:34:a5:1f, Memory 32Mbytes, 3LAN, 1BRI # show environment RTX1100 BootROM Rev.6.02 RTX1100 Rev.8.03.94 (Thu Dec 5 19:06:16 2013) main: RTX1100 ver=e0 serial=N1A088475 MAC-Address=00:a0:de:34:a5:1d MAC-Addr ess=00:a0:de:34:a5:1e MAC-Address=00:a0:de:34:a5:1f CPU: 3%(5sec) 4%(1min) 3%(5min) Memory: 34% used Firmware: exec0 Config. file: config0 Default firmware: exec0 Default config. file: config0 Boot time: 1980/01/03 13:23:42 +09:00 Current time: 1980/01/03 14:56:06 +09:00 Elapsed time from boot: 0days 01:32:24 Security Class: 1, FORGET: ON, TELNET: OFF
> administrator Password: console character ascii login timer 3600 ip route default gateway dhcp lan2 ip lan1 address 192.168.100.1/24 description lan2 PRV/DHCP/225:NURO ip lan2 address dhcp ip lan2 nat descriptor 200 nat descriptor type 200 masquerade nat descriptor address outer 200 primary dhcp service server dhcp server rfc2131 compliant except remain-silent dhcp scope 1 192.168.100.128-192.168.100.254/24 dns server dhcp lan2 dns server select 500226 dhcp lan2 any . dns private address spoof on snmp sysname yamaha-rtx1100 ntpdate ntp.nict.jp schedule at 1 */* 5:00 * ntpdate ntp.nict.jp syslog httpd host lan1 save Saving ... CONFIG0 Done .
tunnel select 1 ipsec ike encryption 1 aes-cbc ipsec ike group 1 modp1024 ipsec ike hash 1 sha ipsec ike pre-shared-key 1 text I2dCOkDKgBjnUPTSMrNP5pHvvowELgkM ipsec tunnel 201 ipsec sa policy 201 1 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 1 3600 ipsec ike pfs 1 on ipsec tunnel outer df-bit clear ipsec ike keepalive use 1 on dpd 10 3 ipsec ike local address 1 118.xxx.yyy.253 ipsec ike remote address 1 13.112.141.58 ip tunnel address 169.254.24.230/30 ip tunnel remote address 169.254.24.229 ip tunnel tcp mss limit 1379 tunnel enable 1 tunnel select none ipsec auto refresh on bgp use on bgp autonomous-system 65000 bgp neighbor 1 10124 169.254.24.229 hold-time=30 local-address=169.254.24.230 bgp import filter 1 equal 0.0.0.0/0 bgp import 10124 static filter 1 tunnel select 2 ipsec ike encryption 2 aes-cbc ipsec ike group 2 modp1024 ipsec ike hash 2 sha ipsec ike pre-shared-key 2 text CKcZbiRyOOgyEJ5nCy3KwW..DQMAY4I5 ipsec tunnel 202 ipsec sa policy 202 2 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 2 3600 ipsec ike pfs 2 on ipsec tunnel outer df-bit clear ipsec ike keepalive use 2 on dpd 10 3 ipsec ike local address 2 118.xxx.yyy.253 ipsec ike remote address 2 52.197.214.91 ip tunnel address 169.254.24.210/30 ip tunnel remote address 169.254.24.209 ip tunnel tcp mss limit 1379 tunnel enable 2 tunnel select none ipsec auto refresh on bgp use on bgp autonomous-system 65000 bgp neighbor 2 10124 169.254.24.209 hold-time=30 local-address=169.254.24.210 bgp import filter 1 equal 0.0.0.0/0 bgp import 10124 static filter 1 bgp import filter 1 equal 192.168.100.0/24 nat descriptor masquerade static 1 1 192.168.100.1 udp 500 nat descriptor masquerade static 1 2 192.168.100.1 esp bgp configure refresh save
# show status tunnel 1
TUNNEL[1]:
Description:
Interface type: IPsec
Current status is Online.
from 1980/01/04 14:49:15.
13630 days 3 hours 27 minutes 29 seconds connection.
Received: (IPv4) 75 packets [4852 octets]
(IPv6) 0 packet [0 octet]
Transmitted: (IPv4) 89 packets [5449 octets]
(IPv6) 0 packet [0 octet]
# show status tunnel 2
TUNNEL[2]:
Description:
Interface type: IPsec
Current status is Online.
from 1980/01/04 14:49:16.
13630 days 3 hours 27 minutes 33 seconds connection.
Received: (IPv4) 76 packets [4904 octets]
(IPv6) 0 packet [0 octet]
Transmitted: (IPv4) 86 packets [5293 octets]
(IPv6) 0 packet [0 octet]
# show ipsec sa sa sgw connection dir life[s] remote-id -------------------------------------------------------------------------- 1 1 isakmp - 28390 13.112.141.58 2 2 isakmp - 28390 52.197.214.91 3 1 tun[001]esp send 3192 13.112.141.58 4 1 tun[001]esp recv 3192 13.112.141.58 5 2 tun[002]esp send 3193 52.197.214.91 6 2 tun[002]esp recv 3193 52.197.214.91 SA[1] Duration: 28390s Local ID: 118.xxx.yyy.253 Remote ID: 13.112.141.58 Protocol: IKE SPI: 68 dc 5a 24 b5 38 44 8f c6 b0 19 8b 22 8e b0 90 Key: ad 47 44 26 b2 84 d8 ad ---------------------------------------------------- SA[2] Duration: 28390s Local ID: 118.xxx.yyy.253 Remote ID: 52.197.214.91 Protocol: IKE SPI: 64 7d 61 81 e7 e8 a5 00 41 1f f5 04 7b 20 2a e4 Key: 33 25 5c 66 3a c6 eb a4 ---------------------------------------------------- SA[3] Duration: 3192s Local ID: 118.xxx.yyy.253 Remote ID: 13.112.141.58 Direction: send Protocol: ESP (Mode: tunnel) Algorithm: AES-CBC (for Auth.: HMAC-SHA) SPI: db 3b 41 db Key: 92 96 97 35 71 36 17 47 12 78 a0 66 e0 62 a3 f5 ---------------------------------------------------- SA[4] Duration: 3192s Local ID: 118.xxx.yyy.253 Remote ID: 13.112.141.58 Direction: receive Protocol: ESP (Mode: tunnel) Algorithm: AES-CBC (for Auth.: HMAC-SHA) SPI: 3d 1d 61 d3 Key: a5 0c bf b2 7c f6 7a 76 ab e1 45 f5 e9 0d e2 87 ---------------------------------------------------- SA[5] Duration: 3193s Local ID: 118.xxx.yyy.253 Remote ID: 52.197.214.91 Direction: send Protocol: ESP (Mode: tunnel) Algorithm: AES-CBC (for Auth.: HMAC-SHA) SPI: 7e b7 69 2b Key: 1b ff 1e 85 68 cc 4e a5 3b 5c 14 31 d8 2f 3c ef ---------------------------------------------------- SA[6] Duration: 3193s Local ID: 118.xxx.yyy.253 Remote ID: 52.197.214.91 Direction: receive Protocol: ESP (Mode: tunnel) Algorithm: AES-CBC (for Auth.: HMAC-SHA) SPI: d2 ef d9 f2 Key: df d2 19 0a a8 79 ed b5 f9 e2 69 64 e6 57 b2 bd ----------------------------------------------------
# show status bgp neighbor BGP neighbor is 169.254.24.229, remote AS 10124, local AS 65000, external link BGP version 4, remote router ID 169.254.24.229 BGP state = Established, up for 00:06:33 Last read 00:00:03, hold time is 30, keepalive interval is 10 seconds Received 41 messages, 0 notifications, 0 in queue Sent 45 messages, 1 notifications, 0 in queue Connection established 1; dropped 0 Last reset never Local host: 169.254.24.230, Local port: 1026 Foreign host: 169.254.24.229, Foreign port: 179 BGP neighbor is 169.254.24.209, remote AS 10124, local AS 65000, external link BGP version 4, remote router ID 169.254.24.209 BGP state = Established, up for 00:06:33 Last read 00:00:03, hold time is 30, keepalive interval is 10 seconds Received 41 messages, 0 notifications, 0 in queue Sent 45 messages, 1 notifications, 0 in queue Connection established 1; dropped 0 Last reset never Local host: 169.254.24.210, Local port: 1027 Foreign host: 169.254.24.209, Foreign port: 179 # show status bgp neighbor 169.254.24.229 received-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path * 10.0.0.0/16 169.254.24.229 100 10124 IGP # show status bgp neighbor 169.254.24.209 received-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path 10.0.0.0/16 169.254.24.209 200 10124 IGP # show status bgp neighbor 169.254.24.209 advertised-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path * 192.168.100.0/24 192.168.100.1 0 IGP # show status bgp neighbor 169.254.24.229 advertised-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path * 192.168.100.0/24 192.168.100.1 0 IGP # show ip route Destination Gateway Interface Kind Additional Info. default 118.240.212.129 LAN2(DHCP) static 10.0.0.0/16 169.254.24.229 TUNNEL[1] BGP path=10124 118.240.212.128/25 118.xxx.yyy.253 LAN2 implicit 169.254.24.208/30 - TUNNEL[2] implicit 169.254.24.228/30 - TUNNEL[1] implicit 192.168.100.0/24 192.168.100.1 LAN1 implicit
# show config # RTX1100 Rev.8.03.94 (Thu Dec 5 19:06:16 2013) # MAC Address : 00:a0:de:34:a5:1d, 00:a0:de:34:a5:1e, 00:a0:de:34:a5:1f, # Memory 32Mbytes, 3LAN, 1BRI # main: RTX1100 ver=e0 serial=N1A088475 MAC-Address=00:a0:de:34:a5:1d MAC-Address=00:a0:de:34:a5:1e MAC-Address=00:a0:de:34:a5:1f # Reporting Date: Jan 4 14:38:53 1980 console character ascii login timer 3600 ip route default gateway dhcp lan2 ip lan1 address 192.168.100.1/24 description lan2 PRV/DHCP/225:NURO ip lan2 address dhcp ip lan2 nat descriptor 200 tunnel select 1 ipsec tunnel 201 ipsec sa policy 201 1 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 1 3600 ipsec ike encryption 1 aes-cbc ipsec ike group 1 modp1024 ipsec ike hash 1 sha ipsec ike keepalive use 1 on dpd 10 3 ipsec ike local address 1 118.xxx.yyy.253 ipsec ike pfs 1 on ipsec ike pre-shared-key 1 text I2dCOkDKgBjnUPTSMrNP5pHvvowELgkM ipsec ike remote address 1 13.112.141.58 ipsec tunnel outer df-bit clear ip tunnel address 169.254.24.230/30 ip tunnel remote address 169.254.24.229 ip tunnel tcp mss limit 1379 tunnel enable 1 tunnel select 2 ipsec tunnel 202 ipsec sa policy 202 2 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 2 3600 ipsec ike encryption 2 aes-cbc ipsec ike group 2 modp1024 ipsec ike hash 2 sha ipsec ike keepalive use 2 on dpd 10 3 ipsec ike local address 2 118.xxx.yyy.253 ipsec ike pfs 2 on ipsec ike pre-shared-key 2 text CKcZbiRyOOgyEJ5nCy3KwW..DQMAY4I5 ipsec ike remote address 2 52.197.214.91 ipsec tunnel outer df-bit clear ip tunnel address 169.254.24.210/30 ip tunnel remote address 169.254.24.209 ip tunnel tcp mss limit 1379 tunnel enable 2 nat descriptor masquerade static 1 1 192.168.100.1 udp 500 nat descriptor masquerade static 1 2 192.168.100.1 esp nat descriptor type 200 masquerade nat descriptor address outer 200 primary nat descriptor type 1000 masquerade nat descriptor address outer 1000 ipcp nat descriptor address inner 1000 auto bgp use on bgp autonomous-system 65000 bgp neighbor 1 10124 169.254.24.229 hold-time=30 local-address=169.254.24.230 bgp neighbor 2 10124 169.254.24.209 hold-time=30 local-address=169.254.24.210 bgp import filter 1 equal 192.168.100.0/24 bgp import 10124 static filter 1 ipsec auto refresh on dhcp service server dhcp server rfc2131 compliant except remain-silent dhcp scope 1 192.168.100.128-192.168.100.254/24 dns server 8.8.8.8 8.8.4.4 dns server dhcp lan2 dns server select 500226 dhcp lan2 any . dns private address spoof on snmp sysname yamaha-rtx1100 httpd host lan1
これでVPN接続成功
もくじ
完成
# show config # RTX1100 Rev.8.03.94 (Thu Dec 5 19:06:16 2013) # MAC Address : 00:a0:de:34:a5:1d, 00:a0:de:34:a5:1e, 00:a0:de:34:a5:1f, # Memory 32Mbytes, 3LAN, 1BRI # main: RTX1100 ver=e0 serial=N1A088475 MAC-Address=00:a0:de:34:a5:1d MAC-Address=00:a0:de:34:a5:1e MAC-Address=00:a0:de:34:a5:1f # Reporting Date: Apr 29 18:20:15 2017 console character ascii login timer 3600 ip route default gateway dhcp lan2 ip lan1 address 192.168.100.1/24 ip lan1 secure filter in 100000 100001 100002 100003 100004 100005 100006 100007 100099 description lan2 PRV/DHCP/225:NURO ip lan2 address dhcp ip lan2 secure filter in 101003 101020 101021 101022 101023 101024 101025 101030 101032 ip lan2 secure filter out 101013 101020 101021 101022 101023 101024 101025 101026 101027 101099 dynamic 101080 101081 101082 101083 101084 101085 101098 101099 ip lan2 nat descriptor 200 tunnel select 1 ipsec tunnel 201 ipsec sa policy 201 1 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 1 3600 ipsec ike encryption 1 aes-cbc ipsec ike group 1 modp1024 ipsec ike hash 1 sha ipsec ike keepalive use 1 on dpd 10 3 ipsec ike local address 1 118.xxx.yyy.253 ipsec ike pfs 1 on ipsec ike pre-shared-key 1 text I2dCOkDKgBjnUPTSMrNP5pHvvowELgkM ipsec ike remote address 1 13.112.141.58 ipsec tunnel outer df-bit clear ip tunnel address 169.254.24.230/30 ip tunnel remote address 169.254.24.229 ip tunnel tcp mss limit 1379 tunnel enable 1 tunnel select 2 ipsec tunnel 202 ipsec sa policy 202 2 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 2 3600 ipsec ike encryption 2 aes-cbc ipsec ike group 2 modp1024 ipsec ike hash 2 sha ipsec ike keepalive use 2 on dpd 10 3 ipsec ike local address 2 118.xxx.yyy.253 ipsec ike pfs 2 on ipsec ike pre-shared-key 2 text CKcZbiRyOOgyEJ5nCy3KwW..DQMAY4I5 ipsec ike remote address 2 52.197.214.91 ipsec tunnel outer df-bit clear ip tunnel address 169.254.24.210/30 ip tunnel remote address 169.254.24.209 ip tunnel tcp mss limit 1379 tunnel enable 2 ip filter 100000 reject * * udp,tcp 135 * ip filter 100001 reject * * udp,tcp * 135 ip filter 100002 reject * * udp,tcp netbios_ns-netbios_dgm * ip filter 100003 reject * * udp,tcp * netbios_ns-netbios_dgm ip filter 100004 reject * * udp,tcp netbios_ssn * ip filter 100005 reject * * udp,tcp * netbios_ssn ip filter 100006 reject * * udp,tcp 445 * ip filter 100007 reject * * udp,tcp * 445 ip filter 100099 pass * * * * * ip filter 101000 reject 10.0.0.0/8 * * * * ip filter 101001 reject 172.16.0.0/12 * * * * ip filter 101002 reject 192.168.0.0/16 * * * * ip filter 101003 reject 192.168.0.0/24 * * * * ip filter 101010 reject * 10.0.0.0/8 * * * ip filter 101011 reject * 172.16.0.0/12 * * * ip filter 101012 reject * 192.168.0.0/16 * * * ip filter 101013 reject * 192.168.11.0/24 * * * ip filter 101020 reject * * udp,tcp 135 * ip filter 101021 reject * * udp,tcp * 135 ip filter 101022 reject * * udp,tcp netbios_ns-netbios_ssn * ip filter 101023 reject * * udp,tcp * netbios_ns-netbios_ssn ip filter 101024 reject * * udp,tcp 445 * ip filter 101025 reject * * udp,tcp * 445 ip filter 101026 restrict * * tcpfin * www,21,nntp ip filter 101027 restrict * * tcprst * www,21,nntp ip filter 101030 pass * 192.168.0.0/24 icmp * * ip filter 101031 pass * 192.168.0.0/24 established * * ip filter 101032 pass * 192.168.0.0/24 tcp * ident ip filter 101033 pass * 192.168.0.0/24 tcp ftpdata * ip filter 101034 pass * 192.168.0.0/24 tcp,udp * domain ip filter 101035 pass * 192.168.0.0/24 udp domain * ip filter 101036 pass * 192.168.0.0/24 udp * ntp ip filter 101037 pass * 192.168.0.0/24 udp ntp * ip filter 101085 pass * 192.168.0.0/24 tcp 587 * ip filter 101099 pass * * * * * ip filter 500000 restrict * * * * * ip filter dynamic 101080 * * ftp ip filter dynamic 101081 * * domain ip filter dynamic 101082 * * www ip filter dynamic 101083 * * smtp ip filter dynamic 101084 * * pop3 ip filter dynamic 101098 * * tcp ip filter dynamic 101099 * * udp nat descriptor masquerade static 1 1 192.168.100.1 udp 500 nat descriptor masquerade static 1 2 192.168.100.1 esp nat descriptor type 200 masquerade nat descriptor address outer 200 primary nat descriptor type 1000 masquerade nat descriptor address outer 1000 ipcp nat descriptor address inner 1000 auto bgp use on bgp autonomous-system 65000 bgp neighbor 1 10124 169.254.24.229 hold-time=30 local-address=169.254.24.230 bgp neighbor 2 10124 169.254.24.209 hold-time=30 local-address=169.254.24.210 bgp import filter 1 equal 192.168.100.0/24 bgp import 10124 static filter 1 ipsec auto refresh on dhcp service server dhcp server rfc2131 compliant except remain-silent dhcp scope 1 192.168.100.128-192.168.100.254/24 dns server 8.8.8.8 8.8.4.4 dns server dhcp lan2 dns server select 500226 dhcp lan2 any . dns private address spoof on snmp sysname yamaha-rtx1100 schedule at 1 */* 06:00 * ntpdate ntp.nict.jp syslog httpd host lan1
これで完成。