寄稿しました。
もくじ
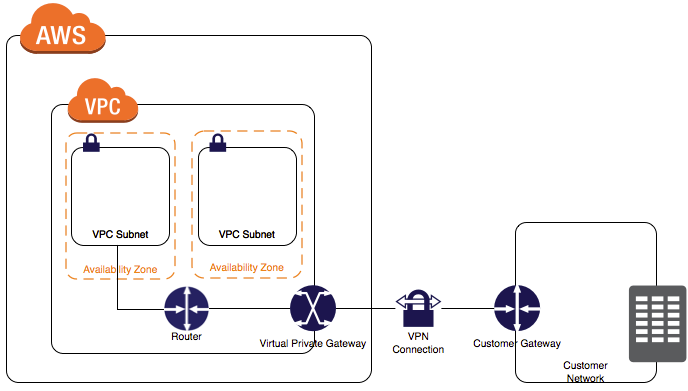
環境

- ルータ:RTX1100
- 接続先クラウド:AWS VPC
- 回線:NURO
- 技術要素:YAMAHA RTX1100, AWS VPC, VPC Subnet、ルートテーブル, AWS VPN Connection , 仮想プライベートゲートウェイ VPN Connection, カスタマーゲートウェイ
# show environment RTX1100 BootROM Rev.6.02 RTX1100 Rev.8.03.94 (Thu Dec 5 19:06:16 2013) main: RTX1100 ver=e0 serial=N1A088475 MAC-Address=00:ho:ge:34:a9:2d MAC-Addr ess=00:a0:de:34:a5:1e MAC-Address=00:a0:de:34:a5:1f CPU: 3%(5sec) 4%(1min) 3%(5min) Memory: 34% used Firmware: exec0 Config. file: config0 Default firmware: exec0 Default config. file: config0 Boot time: 1980/01/03 13:23:42 +09:00 Current time: 1980/01/03 14:56:06 +09:00 Elapsed time from boot: 0days 01:32:24 Security Class: 1, FORGET: ON, TELNET: OFF
工場出荷状態。
ネットワーク
- ルータ側 プライベートアドレス:192.168.10.1
- ルータ側 LAN:192.168.10.0/24
- ルータ側 グローバルIP:xxx.yyy.zzz.aaa
- AWS VPC側 LAN:10.0.0.0/16
- AWS VPC側 サブネット:10.0.0.0/24
初期設定
今回の環境は回線がNUROでPPPoEによるユーザ認証はしません。
> administrator Password: console character ascii login timer 3600 ip route default gateway dhcp lan2 ip lan1 address 192.168.10.1/24 description lan2 PRV/DHCP/225:NURO ip lan2 address dhcp ip lan2 nat descriptor 200 nat descriptor type 200 masquerade nat descriptor address outer 200 primary dhcp service server dhcp server rfc2131 compliant except remain-silent dhcp scope 1 192.168.10.2-192.168.10.190/24 dns server dhcp lan2 dns server select 500226 dhcp lan2 any . dns private address spoof on snmp sysname yamaha-rtx1100 ntpdate ntp.nict.jp schedule at 1 */* 5:00 * ntpdate ntp.nict.jp syslog httpd host lan1
PPPoEによる接続が必要な環境の方
プロバイダとの接続にPPPoEが必要な場合は下記のpp select 1より設定が必要です。
pp select 1 pp always-on on pppoe use lan2 pppoe auto disconnect off pp auth accept pap chap pp auth myname (ISPへ接続するID) (ISPへ接続するパスワード) ppp lcp mru on 1454 ppp ipcp msext on ppp ccp type none ip pp address (ルーターのグローバルIPアドレス) ip pp nat descriptor 1000 pp enable 1
AWSとのVPN接続設定サンプル
tunnel select 1 ipsec ike encryption 1 aes-cbc ipsec ike group 1 modp1024 ipsec ike hash 1 sha ipsec ike pre-shared-key 1 text hogemogehohoho※AWS VPN秘密鍵パスフレーズ ipsec tunnel 201 ipsec sa policy 201 1 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 1 3600 ipsec ike pfs 1 on ipsec tunnel outer df-bit clear ipsec ike keepalive use 1 on dpd 10 3 ipsec ike local address 1 xxx.yyy.zzz.aaa※ルータ側固定IP ipsec ike remote address 1 13.112.141.58 ip tunnel address 169.254.24.230/30 ip tunnel remote address 169.254.24.229 ip tunnel tcp mss limit 1379 tunnel enable 1 tunnel select none ipsec auto refresh on bgp use on bgp autonomous-system 65000 bgp neighbor 1 10124 169.254.24.229 hold-time=30 local-address=169.254.24.230 bgp import filter 1 equal 0.0.0.0/0 bgp import 10124 static filter 1 tunnel select 2 ipsec ike encryption 2 aes-cbc ipsec ike group 2 modp1024 ipsec ike hash 2 sha ipsec ike pre-shared-key 2 text hogemogehohoho※AWS VPN秘密鍵パスフレーズ ipsec tunnel 202 ipsec sa policy 202 2 esp aes-cbc sha-hmac ipsec ike duration ipsec-sa 2 3600 ipsec ike pfs 2 on ipsec tunnel outer df-bit clear ipsec ike keepalive use 2 on dpd 10 3 ipsec ike local address 2 xxx.yyy.zzz.aaa ※ルータ側固定IP ipsec ike remote address 2 52.197.214.91 ip tunnel address 169.254.24.210/30 ip tunnel remote address 169.254.24.209 ip tunnel tcp mss limit 1379 tunnel enable 2 tunnel select none ipsec auto refresh on bgp use on bgp autonomous-system 65000 bgp neighbor 2 10124 169.254.24.209 hold-time=30 local-address=169.254.24.210 bgp import 10124 static filter 1 bgp import filter 1 equal 192.168.10.0/24 bgp configure refresh nat descriptor type 1000 masquerade nat descriptor address outer 1000 ipcp nat descriptor address inner 1000 auto nat descriptor masquerade static 1 1 192.168.10.1 udp 500 nat descriptor masquerade static 1 2 192.168.10.1 esp ipsec auto refresh on dns server 8.8.8.8 8.8.4.4 dns private address spoof on
トンネルが2つあるけれど、AWS VPNとの接続の冗長化の為のものなので、ただ繋げるだけなら1つでも大丈夫です。
RTX1100~RTX1210は上記で動くはず、RTX1000だと少し書き換えが必要かな。
bgp neighbor 1 10124 169.254.24.229 hold-time=30 local-address=169.254.24.230 ↓ bgp neighbor 1 10124 169.254.24.229 hold-time=30
AWSとのVPN接続の確認
トンネル状態の確認を行います。
# show status tunnel 1
TUNNEL[1]:
Description:
Interface type: IPsec
Current status is Online.
from 1980/01/04 14:49:15.
13630 days 3 hours 27 minutes 29 seconds connection.
Received: (IPv4) 75 packets [4852 octets]
(IPv6) 0 packet [0 octet]
Transmitted: (IPv4) 89 packets [5449 octets]
(IPv6) 0 packet [0 octet]
# show status tunnel 2
TUNNEL[2]:
Description:
Interface type: IPsec
Current status is Online.
from 1980/01/04 14:49:16.
13630 days 3 hours 27 minutes 33 seconds connection.
Received: (IPv4) 76 packets [4904 octets]
(IPv6) 0 packet [0 octet]
Transmitted: (IPv4) 86 packets [5293 octets]
(IPv6) 0 packet [0 octet]
鍵交換が出来ていることを確認
# show ipsec sa sa sgw connection dir life[s] remote-id -------------------------------------------------------------------------- 1 1 isakmp - 28390 13.112.141.58 2 2 isakmp - 28390 52.197.214.91 3 1 tun[001]esp send 3192 13.112.141.58 4 1 tun[001]esp recv 3192 13.112.141.58 5 2 tun[002]esp send 3193 52.197.214.91 6 2 tun[002]esp recv 3193 52.197.214.91
BGPの確認
# show status bgp neighbor BGP neighbor is 169.254.24.229, remote AS 10124, local AS 65000, external link BGP version 4, remote router ID 169.254.24.229 BGP state = Established, up for 00:06:33 Last read 00:00:03, hold time is 30, keepalive interval is 10 seconds Received 41 messages, 0 notifications, 0 in queue Sent 45 messages, 1 notifications, 0 in queue Connection established 1; dropped 0 Last reset never Local host: 169.254.24.230, Local port: 1026 Foreign host: 169.254.24.229, Foreign port: 179 BGP neighbor is 169.254.24.209, remote AS 10124, local AS 65000, external link BGP version 4, remote router ID 169.254.24.209 BGP state = Established, up for 00:06:33 Last read 00:00:03, hold time is 30, keepalive interval is 10 seconds Received 41 messages, 0 notifications, 0 in queue Sent 45 messages, 1 notifications, 0 in queue Connection established 1; dropped 0 Last reset never Local host: 169.254.24.210, Local port: 1027 Foreign host: 169.254.24.209, Foreign port: 179
BGP StateがEstablishedになっていれば接続できています。
BGPネイバーのルート確認
# show status bgp neighbor 169.254.24.229 received-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path * 10.0.0.0/16 169.254.24.229 100 10124 IGP # show status bgp neighbor 169.254.24.209 received-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path 10.0.0.0/16 169.254.24.209 200 10124 IGP
# show status bgp neighbor 169.254.24.209 advertised-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path * 192.168.10.0/24 192.168.10.1 0 IGP # show status bgp neighbor 169.254.24.229 advertised-routes Total routes: 1 *: valid route Network Next Hop Metric LocPrf Path * 192.168.10.0/24 192.168.10.1 0 IGP
確立されています。
ルート確認
# show ip route Destination Gateway Interface Kind Additional Info. default 118.240.212.129 LAN2(DHCP) static 10.0.0.0/16 169.254.24.229 TUNNEL[1] BGP path=10124 118.240.212.128/25 xxx.yyy.zzz.aaa LAN2 implicit 169.254.24.208/30 - TUNNEL[2] implicit 169.254.24.228/30 - TUNNEL[1] implicit 192.168.10.0/24 192.168.10.1 LAN1 implicit
AWS VPC VPN接続からの確認
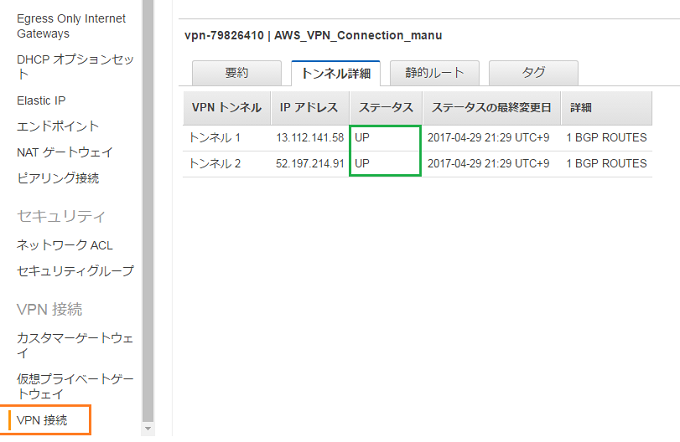
【サービス】>> 【VPC】>> 【VPN接続】>> 【トンネル詳細】を選択します。
ステータスがUPになっていれば良いです!
AWS上のEC2にプライベート接続しよう